Basic differences between
classical and quantum cryptography
Abstract
Data protection is crucial in today’s digital age, where billions of pieces of personal and corporate information are stored and transmitted online.
With the rise of cybersecurity threats, safeguarding data is essential for personal data security, preserving corporate secrets, and national security.
Classical cryptography, such as RSA(Riverst-Shamir-Andleman) and ECC (Elliptic-curve cryptography), has ensured data transmission security for decades, but the advancement of quantum computers poses new challenges. These machines will be capable of breaking current cryptographic algorithms, which rely on the difficulty of factoring large numbers or elliptic curve cryptography.
Quantum cryptography, particularly quantum key distribution (QKD), offers a solution by allowing the secure distribution of keys deemed unbreakable. This is based on the laws of quantum mechanics.
Quantum cryptography lets us create communication systems where security is based solely on the laws of physics and some basic assumptions about the hardware we use for encryption, making it incredibly difficult for anyone to breach. [1]
This paper provides an overview of the principles and state-of-the-art of quantum cryptography, comparing it to classical cryptography. It also mentions post-quantum cryptography for comparison.
Introduction
It’s important to understand why there is a need for new cryptographic solutions and what dangers threaten the current encryption methods.
Technology is evolving rapidly and companies and governments are at risk if they use devices with outdated encryption methods. The development of the Quantum Computer is a case in point.
The fundamental difference between a classical computer and a quantum computer is the storage of information: while in conventional computers information is stored in bits, a quantum computer handles a series of quantum bits. A quantum bit can contain zero, one or their quantum superposition, allowing an infinite number of states.
This means that Quantum computers can solve mathematical problems in minutes that classical computers do not have the capacity to do.
The field of science is constantly developing, so it is worth comparing the protection of IT systems to it as soon as possible.
2023 In October 2023, the first quantum computer above 1,000 qubits was announced. It is predicted that this number could increase to 1,000,000 qubits by 2030 – a significant increase – and it is predicted that within 10 years we could reach 20,000,000 qubits. [2]
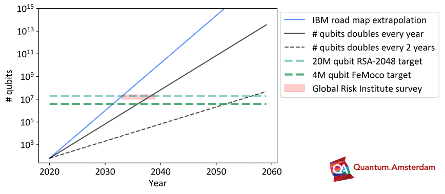
This also means, according to current research, that by the early 2030s, basic and traditional cryptographic procedures such as RSA will be crackable using Quantum computers. In anticipation of this threat, post-quantum cryptography is working to develop classical cryptographic systems that are secure against quantum computers. [3]
The intrinsic randomness of quantum states and measurements can be exploited to generate truly random bits. Entanglement enables the creation of identical sets of random bits at two separate locations, regardless of their distance apart.
Also, quantum states have the property that they cannot be copied perfectly, unlike classical bits. If an attacker tries to access information hidden in quantum states, it must interact with the quantum state in some way, leading to noticeable changes in the state. As a result, communicating parties detect an attempted attack before confidential information is exchanged. Quantum key distribution (QKD) is the process through which a secure key is established using principles of quantum mechanics.
Differences in cryptography
Types of Cryptography
There are basically three types of cryptography: Classical, Post-Quantum and Quantum cryptography.
The common objective of all three is to encrypt data and ensure its security, integrity, and authenticity.
The fundamental difference is how the data is protected.
- Classical cryptography uses complex mathematical problems to counter threats. It is not suitable for quantum threat prevention.
- Post-Quantum Cryptography is the solution of the present era to prepare for and defend against quantum attacks as well. It is also based on mathematical problems, however, it is much more complex than those used in classical cryptography.
- Quantum cryptography now exploits the properties of quantum mechanics rather than mathematical problems to protect against quantum threats
The limits of classical cryptography
One of the most widely used asymmetric encryption methods is RSA. In this protocol, the private key is generated using a pair of randomly chosen prime numbers, multiplied by a semiprime number. The corresponding public key is derived from this semiprime.
Modern implementations use hundreds of prime numbers, which there is no known algorithm that a conventional computer can crack in a realistic time frame.
However, Shor’s algorithm, presented in 1994, was already able to prove that the factorization problem can be solved in polynomial time using quantum computers. With the development of quantum computers, we can feel the danger of these algorithms being hacked ever closer.
Furthermore, the security of Elliptic-curve Cryptography (ECC) is based on the difficulty of mathematical operations on elliptic curves, in particular the elliptic curve discrete logarithm problem (ECDLP). While this problem is extremely time-consuming for current classical computers, the potential evolution of quantum computers poses a threat. Furthermore, the emergence of new mathematical methods or algorithms that solve ECDLP more efficiently could also undermine the security of ECC, even before the diffusion of quantum technology.
In reality, this situation presents a substantial risk to data confidentiality as it stands today: An adversary could store information encrypted with any vulnerable encryption algorithm, such as RSA, in its encrypted form and then decrypt it later upon obtaining access to a quantum computer.
If the data need to stay secret for a long time, it means that quantum computers are already a risk to keeping data safe today.
Keys at Risk:
- Advanced Encryption Standard (AES) 256 – Larger output needed
- Secure Hash Algorithm (SHA) 256 and SHA-3 – Larger output needed
- Rivest-Shamir-Adelman (RSA encryption) – No longer secure
- Elliptic Curve Cryptography (ECDSA and ECDH) – No longer secure
- Digital Signature Algorithm (DSA) – No longer secure
Continuing from the previous explanation, “larger output needed” signifies a requirement for increased cryptographic strength to withstand potential quantum computer attacks. This directive implies that the encryption or hashing process must produce longer strings of bits. In practical terms, a longer output for encryption keys or hash values substantially expands the computational effort required to crack them through brute force attacks, including those executed by quantum computers.
“No longer secure” simply implies that certain encryption methods are no longer effective against contemporary or emerging threats, particularly those posed by quantum computing advancements. It signifies that these algorithms cannot ensure reliable data protection anymore, prompting the need for alternative, more secure encryption methods.
Entrust is a participating member of the Internet Engineering Task Force (IETF) and collaborates with NIST to identify new post-quantum cryptography standards for the post-quantum world. It’s critical to begin planning to replace hardware, software, and services that use public-key algorithms now so that informatiosn is protected from the future post-quantum threat. [4],[5]
Post-quantum cryptography compared to the classical
Post-quantum cryptography is currently undergoing active research and development, exploring various new cryptographic algorithms to ensure security and feasibility in the face of emerging quantum computing threats. This applies not only to quantum computers, but also to the ever-increasing power of classical computers.
A fundamental difference from the classical one and one of the goals of PQC is to create more complex algorithms:
- McEliece Cryptosystem: This method uses error-correction tricks, like the ones used to fix typos, to scramble your message. It’s great against future attacks, but the keys to unlock it are a bit bulky.
- Lattice-based Cryptography: This approach builds encryption keys from complex mathematical structures called lattices. It’s strong against both regular computers and future quantum ones.
- Code-based Cryptography: Similar to McEliece, this method uses error-correcting codes for security. It’s good against future attacks, but again, the keys can be a bit on the large side.
- Hash-based Cryptography: This is a simpler method that uses functions like fingerprint scanners to scramble data. It’s easy to use and doesn’t need huge keys, but it might not be the fastest.
- Multivariate Cryptography: This method uses complex math problems to lock your message. It has compact keys, but some tricky attacks might be able to crack it.
PQC algorithms usually require more complex computations than the classical ones for encryption and decryption. This can result in longer processing times and may require more powerful hardware to implement. They also often require larger key sizes to achieve the right level of security compared to classical algorithms. This makes it difficult to store and exchange keys.
The National Institute of Standards and Technology (NIST) launched a competition to select the best candidate for the expected standard.
The NIST has defined several criteria for selecting these algorithms, which provide protection against both traditional and quantum attacks.
| Level | Security Description |
| I. | At least as hard to break as AES128 (exhaustive key search) |
| II. | At least as hard to break as SHA256 (collision search) |
| III. | At least as hard to break as AES192 (exhaustive key search) |
| IV. | At least as hard to break as SHA384 (collision search) |
| V. | At least as hard to break as AES256 (exhaustive key search) |
In this context, the primary criterion revolves around the efficacy of classical algorithms, with the objective being the identification of quantum-resistant alternatives capable of surpassing them in performance. Furthermore, various ancillary considerations were taken into account, including interoperability with established networks and protocols, resilience against side-channel attacks, and mitigation of diverse forms of exploitation.
One such algorithm selected for standardisation is CRYSTALS-KYBER. It uses lattice-based cryptography to establish secure communication between two parties. It is relatively simple and efficient compared to other PQC algorithms.
By comparison, algorithms such as Crystals-Kyber are slower than the classical AES-256 in terms of performance, due to their greater complexity and increased memory requirements. In addition, they have a larger key size compared to AES-256.
This does not mean complete security for the future. As quantum computers become more powerful and new quantum algorithms are developed, we need to keep updating our understanding of which math problems are still considered safe. [5][6][7]
Differences in Quantum Cryptography
Just like post-quantum cryptography aims to safeguard data against quantum threats, quantum cryptography pursues the same goal.
While classical cryptography encodes information using bits, quantum cryptography utilizes qubits, echoing the design principles of quantum computers.
This approach, distinct from traditional encryption methods that rely on mathematical algorithms, depends on the principles of quantum mechanics for ensuring security.
Quantum key distribution (QKD), a key example of this technology, allows for secure communication by taking advantage of the unpredictable behavior of quantum particles. Theoretically, QKD is impervious to the progress of quantum computing, grounded in the unalterable laws of nature.
However, its practical application is not without challenges, necessitating precise configuration and specialized equipment, including dedicated optical fibers and photon emitters for data transmission. Establishing a QKD network, especially on a large scale, can be a costly venture, potentially running into millions of dollars.
Despite its inherent theoretical security, the real-world effectiveness of QKD greatly depends on its correct implementation and strict adherence to operational protocols.
While the theory behind QKD is strong, practical implementation faces hurdles. Imperfect equipment and environmental noise can disrupt the delicate quantum signals. Different QKD protocols address these issues in varying ways. Some protocols make specific assumptions about the devices used, impacting the overall security level achieved. Researchers are constantly refining these protocols to optimize security and practicality for real-world scenarios.
Unlike traditional encryption methods that rely on complex math (which can be broken with stronger computers), quantum cryptography harnesses the laws of quantum mechanics to create unbreakable codes. This means even the most powerful computers wouldn’t be able to crack these codes. While implementing quantum cryptography is currently complex and expensive, it’s actually more achievable than building full-fledged quantum computers.
Challenges like reliable quantum memory still need to be addressed, especially for long distances. However, the requirements for secure communication (quantum key distribution) are less demanding compared to the needs of a universal quantum computer.
Reports on QKD and QC may “guarantee” complete security based on the laws of physics; however, according to the National Security Agency, this is only possible through the precise work of engineers, which has an extremely low tolerance for error. The following five technical limitations have been identified in relation to QKD and QC:
- Quantum key distribution is only a partial solution.
- Quantum key distribution requires special purpose equipment.
- Quantum key distribution increases infrastructure costs and insider threat risks.
- Securing and validating quantum key distribution is a significant challenge.
- Quantum key distribution increases the risk of denial of service.
Referring to these, they claim that QC systems are unbreakable, and in the future there will be no need to use new and increasingly difficult algorithms for encryption methods. [1][8]
References
[1] Renato Renner and Ramona Wolf – Quantum Advantage in Cryptography, ETH Zurich, 8093 Zürich, Switzerland, 2023, https://arc.aiaa.org/doi/10.2514/1.J062267
[2] Atom Computing – Quantum startup Atom Computing first to exceed 1,000 qubits, October 24, 2023, https://atom-computing.com/quantum-startup-atom-computing-first-to-exceed-1000-qubits/
[3] Koen Groenland (Quantum Amsterdam) – Part 5 – Timelines: When can we expect a useful Quantum Computer?, 2024, https://www.quantum.amsterdam/part-5-when-can-we-expect-a-useful-quantum-computer-a-closer-look-at-timelines/
[4] Entrust – A Comprehensive Guide to Quantum-Resistant Cryptography and Encryption , https://www.entrust.com/resources/learn/post-quantum-cryptography-and-encryption
[5] NIST – Post-Quantum Cryptography, 2024, https://csrc.nist.gov/projects/post-quantum-cryptography
[6] NIST – The Beginning of the End: The First NIST PQC Standards, 2022, https://csrc.nist.gov/csrc/media/Presentations/2022/the-beginning-of-the-end-the-first-nist-pqc-standa/images-media/pkc2022-march2022-moody.pdf
[7] Duc-Thuan Dam, Thai-Ha Tran, Van-Phuc Hoang , Cong-Kha Pham and Trong-Thuc Hoang – A Survey of Post-Quantum Cryptography: Start of a New Race, 2023, https://www.mdpi.com/2410-387X/7/3/40
[8] National Security Agency – Quantum Key Distribution (QKD) and Quantum Cryptography (QC), https://www.nsa.gov/Cybersecurity/Quantum-Key-Distribution-QKD-and-Quantum-Cryptography-QC/

